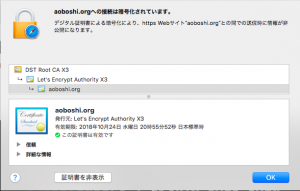
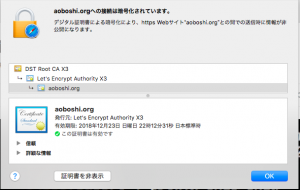
当ブログは常時SSL化をしていますが、期限切れまで1ヶ月を切ったので、9/24に更新をしてみました。
Let’s Encryptは「certbot renew」コマンドで更新が出来ます。
とりあえずそのまま打つと、
$ sudo certbot renew
Saving debug log to /var/log/letsencrypt/letsencrypt.log
——————————————————————————-
Processing /etc/letsencrypt/renewal/aoboshi.org.conf
——————————————————————————-
Cert is due for renewal, auto-renewing…
Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org
Renewing an existing certificate
Performing the following challenges:
tls-sni-01 challenge for aoboshi.org
——————————————————————————-
The program apache2 (process ID 26473) is already listening on TCP port 443.
This will prevent us from binding to that port. Please stop the apache2 program
temporarily and then try again. For automated renewal, you may want to use a
script that stops and starts your webserver. You can find an example at
https://certbot.eff.org/docs/using.html#renewal . Alternatively you can use the
webroot plugin to renew without needing to stop and start your webserver.
——————————————————————————-
Cleaning up challenges
Attempting to renew cert from /etc/letsencrypt/renewal/aoboshi.org.conf produced an unexpected error: At least one
of the required ports is already taken.. Skipping.
——————————————————————————-
Processing /etc/letsencrypt/renewal/www.aoboshi.org.conf
——————————————————————————-
Cert not yet due for renewal
The following certs are not due for renewal yet:
/etc/letsencrypt/live/www.aoboshi.org/fullchain.pem (skipped)
All renewal attempts failed. The following certs could not be renewed:
/etc/letsencrypt/live/aoboshi.org/fullchain.pem (failure)
1 renew failure(s), 0 parse failure(s)
$
apacheを落としてくださいと表示をされたので、「systemctl stop apache2」で停止、
再度実施すると、
$ sudo certbot renew
Saving debug log to /var/log/letsencrypt/letsencrypt.log
——————————————————————————-
Processing /etc/letsencrypt/renewal/aoboshi.org.conf
——————————————————————————-
Cert is due for renewal, auto-renewing…
Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org
Renewing an existing certificate
Performing the following challenges:
tls-sni-01 challenge for aoboshi.org
/usr/lib/python2.7/dist-packages/OpenSSL/rand.py:58: UserWarning: implicit cast from ‘char *’ to a different pointe
r type: will be forbidden in the future (check that the types are as you expect; use an explicit ffi.cast() if they
are correct)
result_code = _lib.RAND_bytes(result_buffer, num_bytes)
Waiting for verification…
Cleaning up challenges
Generating key (2048 bits): /etc/letsencrypt/keys/0002_key-certbot.pem
Creating CSR: /etc/letsencrypt/csr/0002_csr-certbot.pem
——————————————————————————-
new certificate deployed with reload of apache server; fullchain is
/etc/letsencrypt/live/aoboshi.org/fullchain.pem
——————————————————————————-
——————————————————————————-
Processing /etc/letsencrypt/renewal/www.aoboshi.org.conf
——————————————————————————-
Cert not yet due for renewal
The following certs are not due for renewal yet:
/etc/letsencrypt/live/www.aoboshi.org/fullchain.pem (skipped)
Congratulations, all renewals succeeded. The following certs have been renewed:
/etc/letsencrypt/live/aoboshi.org/fullchain.pem (success)
$
「aoboshi.org」の証明書更新は問題なくできました。
「www.aoboshi.org」に関しましては、1ヶ月以上期限があるので更新不要とスキップされました。
その後、落としたapacheを「systemctl start apache2」で立ち上げてもWebサイトに接続できなくなりましたが、
「systemctl restart apache2」で再起動したら無事接続できるようになりました。
数日後、www.aoboshi.orgの証明書も更新しようと思い、
まず「certbot certificates」で証明書の状態を確認したところ、
# certbot certificates
Saving debug log to /var/log/letsencrypt/letsencrypt.log
——————————————————————————-
Found the following certs:
Certificate Name: aoboshi.org
Domains: aoboshi.org
Expiry Date: 2018-12-23 13:12:31+00:00 (VALID: 85 days)
Certificate Path: /etc/letsencrypt/live/aoboshi.org/fullchain.pem
Private Key Path: /etc/letsencrypt/live/aoboshi.org/privkey.pem
Certificate Name: www.aoboshi.org
Domains: www.aoboshi.org
Expiry Date: 2018-12-26 11:21:35+00:00 (VALID: 88 days)
Certificate Path: /etc/letsencrypt/live/www.aoboshi.org/fullchain.pem
Private Key Path: /etc/letsencrypt/live/www.aoboshi.org/privkey.pem
——————————————————————————-
#
www.aoboshi.orgについても更新がされていました。
更新をした覚えはないので調べたところ、
$ sudo systemctl list-timers
NEXT LEFT LAST PASSED UNIT AC
Sun 2018-09-30 09:03:46 UTC 4h 5min left Sat 2018-09-29 09:03:46 UTC 19h ago systemd-tmpfiles-clean.timer sy
Sun 2018-09-30 12:00:00 UTC 7h left Sun 2018-09-30 00:00:01 UTC 4h 57min ago certbot.timer ce
2 timers listed.
Pass –all to see loaded but inactive timers, too.
$
日次でアップデートを実行する設定がLet’s Encrypt設定時にsystemdに組み込まれていたので、自動で更新されていたことがわかりました。